Hardly a day goes by without the media reporting on data theft by phishing, Trojans and so forth. The RWTH Aachen University has also been attacked recently. Already for several months, our mailboxes have been flooded with SPAM mails. For us as IT provider of the RWTH Aachen University this means that we do not want to let you fall into the phishing traps and other similar dangers.
In this blog post, you will find everything you need to know to protect your data and mailboxes from phishing, so that data theft does not happen in the first place.
What happened so far? Phishing Attack with Fake RWTH Mail App Interface
On January 29th, 2020, 1.418 RWTH e-mail accounts were contacted as part of a phishing attack. The RWTH members received e-mails containing, among other things, a link to a fake web interface that was almost identical to the RWTH login mask for the RWTH Mail App. The fake RWTH Mail App is hardly recognisable as fraud to the naked eye.
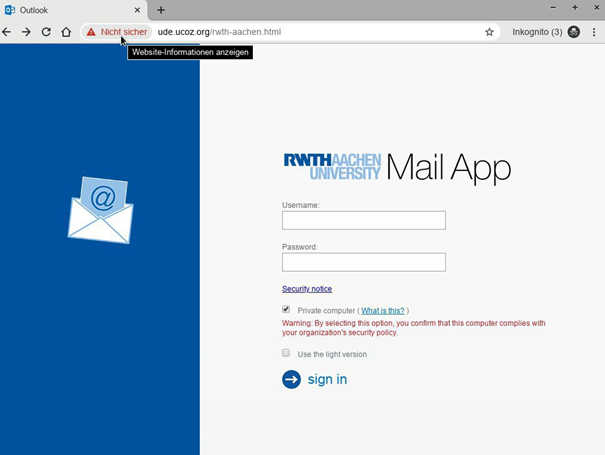
Keep your eyes open when surfing: Fake web interface of the RWTH Mail App. The latest phishing attempt. The URL clearly shows that it is not an official RWTH web application.
Source: Own illustration
The Consequence
If you enter your access data in this fake login mask, they are tapped without encryption. This gives the attacker access to your mailbox –and probably much more. The RWTH Mail App is one of the most used web applications of the university. Almost all members of the RWTH have at least one e-mail address that can be accessed via this application. Unfortunately, it has happened that a few users have entered their login data in the fake interface. In the course of this, the responsible department has taken all necessary protective measures and those concerned have been informed. Basically, something like this can happen to anyone. The only thing that is important is to handle the data carefully and report it to the IT-ServiceDesk if you face security risks in the world wide web.
For this reason, the provider of the fake website was informed and the URL was blocked in order to eliminate the source of danger as quickly as possible.
What you can do to be on the safe side?
- First of all, we all have to check the websites we surf for authenticity. You can do this by checking the link or URL in your browser. Often your browser already tells you if it is probably not a secure site you are trying to enter. The red exclamation mark is your additional warning.
- Do you know the presumed RWTH-URL/link or is it even striking? Then please, report it immediately to the IT-ServiceDesk.

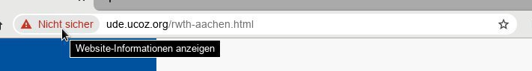
Both browser and URL indicate that the page is not secure. Therefore please look explicitly into the browser line!
Source: Own illustration
- The RWTH Single Sign-On applications, such as RWTHmoodle, RWTHonline or the RWTH Selfservice always start with “sso.rwth-aachen.de”. In a direct comparison with the fake login mask of the RWTH Mail App this becomes clear again (see above).
- Please, also pay attention to the correct spelling in the URL. Even small deviations like the triple-a in “https://rwth-aaachen.de/” are potential danger spots when surfing the web.
- If you are not sure and want to use a trusted source, first go to IT Center Help. Here we have the instructions for our IT-Services ready, but also always the authentic links to the applications.
- From the My IT Center Portal you can also access a variety of web applications used at RWTH. These Links are save to use.
- Make sure you have read the safety instructions we have provided in the documentation portal. Here you can find out how to check a website for authenticity in detail.
The Phishing Site is gone. What now?
A fake website rarely comes alone. Again and again, fake websites are created to steal and access personal data such as login credentials. We will keep up to date on all the channels available to us on the subject of phishing and online security. That is why we recommend that you regularly keep an eye on our latest news and social media articles.
With the instructions, screenshots and recommendations for action and up-to-date information, we do what we can to protect you from phishing and the like.
Here again, all links and sources worth knowing:
- RWTH Aachen University Mail App: https://mail.rwth-aachen.de/owa
- My IT Center Portal
- Announcements on the IT Center website
- Safety Instructions in IT Center Help
- Contact: IT-ServiceDesk
Make sure you also check out the videos on detection of senders, attachments and links:
Responsible for the content of this article are Nicole Filla and Thorsten Kurth.





Wie sehr kann man eigentlich suggerieren, dass Seiten, die https machen, legitim sind? Welch ein Glück, dass sich die Phisher keine teuren Zertifikate leisten können!
(ja, mir ist bewusst, dass das nirgends im Text steht, aber die Bilder legen genau das nahe und wer liest schon den Text?)
Hallo Frank Nord,
vielen Dank für den Kommentar zu unserem Phishing-Beitrag. Wir möchten die Frage sehr gerne beantworten, benötigen diesbezüglich noch einige nähere Informationen. Wir möchten unsere Leser so gut wie möglich informieren und freuen uns daher über eine Rückmeldung.
Lassen Sie uns gerne wissen, an welcher Stelle genau die Suggestion naheliegt, dass “https” als Indikator auf legitime und somit unbedenkliche Seiten schließen lässt? Unser Ziel ist es, unseren Lesenden alle notwendigen Tipps mitzugeben, um sicher auf RWTH-Seiten im www unterwegs zu sein.
Viele Grüße
das IT Center-Blogteam