Kategorie: ‘IT-Security’
Which Browser Is the Most Secure?

Source: Safer Internet Day
To mark Safer Internet Day, we want to raise awareness of online safety and help you to better protect your digital environment. In an increasingly digitalized world where online security is becoming more and more important, choosing the right browser is a crucial step in protecting yourself from cybercrime and unwanted access. But which browser is the most secure? In this article, we have done some research and provide you with an overview of the most popular browsers and their security features. You can also read our previous article to find out more about internet security.
European Data Privacy Day 2025

Source: Freepik
Every year on January 28 is European Data Privacy Day – a date that reminds us of the importance of protecting our personal data and privacy in the digital world. We at the IT Center take this day as an opportunity to draw attention to key aspects of data protection. We already emphasised the importance of protecting our personal data in last year’s article.
Between Viruses and Worms

Source: Freepik
With the advent of the Internet in our everyday lives, the risk of malware such as viruses, worms and Trojans has increased dramatically. What began in the 1980s with distribution via floppy discs and CD-ROMs now takes place almost exclusively via the Internet. Various techniques and technologies make modern malware more inconspicuous and at the same time more dangerous – from stealthy data theft to automatic distribution via botnets.
Zero-Day Vulnerabilities

Source: Own Illustration
Imagine working every day on a computer that seems to run smoothly. Everything works as usual – until one day a security problem is discovered that nobody knew about. Suddenly, a security vulnerability is discovered that attackers have known about for weeks or even months and taken advantage of undetected. This type of vulnerability is known as a zero-day vulnerability. In this blog post, we’ll explore what exactly zero-day vulnerabilities are, why they are particularly dangerous and how best to deal with them.
Updates Again! – Why Are Regular Software Updates So Important?

Source: Stockvault
An update is the updating of the version of a software, information or version. In the case of software updates, for example, a distinction is made between security and firmware updates, and in the case of information updates, for example, between situation, news and status updates. Version updates usually refer to technical devices.
Beware of Tech Support Scams: How You Can Protect Yourself

Source: Freepik
In today’s digital world, we are constantly connected to technology – whether it’s through our smartphones, computers or other electronic devices. Unfortunately, there are people who take advantage of this fact to scam the unsuspecting. One common scam that many fall victim to is the tech support scam. In this blog post, we want to explain how the scam works and how you can protect to protect yourself.
Firewalls – The OSI Model

Source: Freepik
Welcome to the third and final part of our blog series on firewalls! In the first post we looked at the role of firewalls, and in the second we looked at the types of firewalls. In this post, we take a look at the OSI model (Open Systems Interconnection Model) and the different levels at which firewalls can operate.
Halloween: The Nightmares of Cyber Security

Source: Freepik
Fear. A feeling that probably all of us are familiar with. Especially around Halloween, the potential for scares increases. Be it the fear of disguised, made-up figures or even the worry that your sensitive data will fall into the hands of unauthorized persons. Perhaps it’s no coincidence that October of all months is IT Security Month? In this article, we take a look at a few “IT horror stories”, how you can protect yourself from them and share some interesting figures.
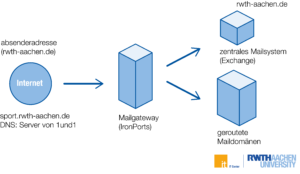
Email Security – Evaluation and Application of the SPF Policy
In this post of our email security series, we would like to inform you about an upcoming tightening of the SPF policy that will apply to RWTH Aachen University as of December 5, 2024. The change will prevent RWTH email addresses from being used as sender addresses by mail servers outside of RWTH Aachen University in the future. This will further increase email security at our university. Please note that this article is mainly intended for mail administrators of RWTH institutions. (*)