IT Center on the road – we are in Dublin for you!
From June 21 to 23, 2023 the “Customer Advisory Council”, short CAC, of the company Dell took place in Dublin, Ireland. In order to support this event as a Dell customer with questions, suggestions and ideas for better cooperation, Peter Watzlawik traveled there on behalf of the IT Center and the “Service and Communication” group, which takes care of client tenders. In the following article, we will give you some exciting insights into the meeting.
DaSi-Day 2023 in Aachen
Finally, the time had come: After almost three years of work in the Datensicherung.nrw project, which started in the summer of 2020 under Corona conditions, the first “DaSi-Day” took place on June 30, 2023 as a face-to-face meeting in the imperial city Aachen at the IT Center of RWTH Aachen University.
Unveiling the Mysteries of 42

Source: Freepik
In the vast world of information technology, there are numerous
fascinating stories,
legends, and references that capture the imagination of tech enthusiasts.
Among these is the enigmatic number 42,which holds a special place in the hearts of IT aficionados. Let’s embark on a journey to unravel the significance of 42 and its intriguing connection to the realm of IT.
Tips and Tricks for Microsoft OneNote
OneNote – is part of the Office package, but it is still not as well known as Word, Excel or PowerPoint.
Although, OneNote is much more useful than expected.

Source: Unsplash
Put simply, OneNote serves as a digital notebook. Not only can notes be created with the keypad, but handwritten notes can also be recorded with the mouse, touchpad or on a touchscreen display.
But this tool can do so much more. Notes that would otherwise be chaotically scattered in various folders can be clearly structured here and filled with various digital content and media. If you don’t like loose paper lying around and don’t want to have Post-Its stuck everywhere, this is the perfect alternative.
Whether you’re a student, a professional, or just like to keep things tidy, we have tips and tricks to help you get the most out of the tool.
The New IT Center Key Visual
The IT Center has a new key visual. The key visual, which we developed for marketing purposes, will be seen in many places in the future, in addition to the IT Center logo.
Whether on merchandise, the web or on print products – the key visual is versatile. In addition to the common logo, the key visual allows a clear identification of the IT Center in the RWTH Aachen University logo system.
The IT Center Picture Puzzle: IT Center Management
#MeetMeWednesday: Our blog series “The IT Center Picture Puzzle” is drawing to a close, and to cap it all off, we have a particularly interesting interview in store for you. This time, the IT Center Management, Professor Müller and Mr. Bündgens, answer our questions. They talk about their daily tasks as well as about exciting projects and developments that will soon take place at the IT Center.
By the way, the key word we were looking for was “leadership”. Could you guess it? Find out more in this article.
RWTHmoodle User Survey 2023 – Help Us Improve Your Learning Experience!
It’s that time again! The annual RWTHmoodle User Survey starts today on July 10, 2023 and runs until July 30, 2023. You have the opportunity to share your experience with the system and give us valuable feedback now if you have used RWTHmoodle and were authorized in at least one learning session during the summer semester 2023. Together, we can further improve RWTHmoodle and adapt the support offering accordingly.
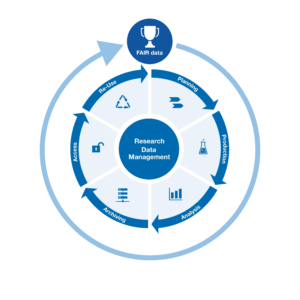
RDM at RWTH Aachen University
You want to know more about Research Data Management at RWTH Aachen University? In this article you will learn general information about RDM and how you can keep up to date about news, new developments and events.
#Goodtoknow – our services in the spotlight

Source: Freepik
We stay connected!
In the first part of our series, you already got to know our collaboration tools Sciebo and Gigamove. In the second part, you got an impression of our diverse communication tools and maybe discovered one or two new ones for you.
Have you already been able to use some of them? Which ones were new to you and which ones do you already use? Feel free to let us know in a comment!
Today’s post concludes this little #goodtoknow series focusing on VPN and eduroam.
Cybersecurity 101: Protecting the Digital Footprint in the Digital Age

Source: Own Illustration
In today’s digital age, our lives are increasingly intertwined with the online world. From social media profiles to online banking accounts, we leave a digital footprint that can be vulnerable to cyber threats. Protecting our digital presence and maintaining online privacy is more important now than ever. In this blog post, we’ll go over the basics of cybersecurity and provide practical tips for protecting your digital footprint.