Source: Freepik
In our first article on the topic of e-mail security, we gave an insight into the historical development of email. We briefly explained how email exchange works and referred to the statistics of the email service at RWTH Aachen University.
Today we’ll tell you about the transmission protocol “Simple Mail Transfer Protocol” (SMTP) and its pitfalls.
The SMTP Protocol
The SMTP protocol is a very old protocol. It processes the sender or the recipient of an e-mail message via corresponding meta information. The meta information includes the addresses of the sender and recipient or the date and subject of the message.
This meta information belongs to a mail and is contained in the so-called mail header. When sending an e-mail, the sending client also separately informs the outgoing mail server of the sender and the recipient. This information forms the mail envelope. The mail envelope is then used by all mail servers involved in the delivery of the e-mail. When the e-mail is delivered to the destination mailbox, this mail envelope is removed again. However, this is exactly where one of the problems lies.
Analysis and Main Problems of This Protocol From a Security Point of View
The SMTP protocol in its simplest version does not include any authentication and authorisation layer. This means that the sender specified by the client in the mail envelope is not checked by the server. Thus, it is theoretically possible for anyone to send e-mails with any other sender address. As one quickly realises, this mechanism opens all doors for phishing and SPAM.
A second problem is that there are three sender addresses in each email. One is the envelope sender address. As described above, this information is deleted when an email is received. However, it is mainly responsible for the actual delivery of an e-mail.
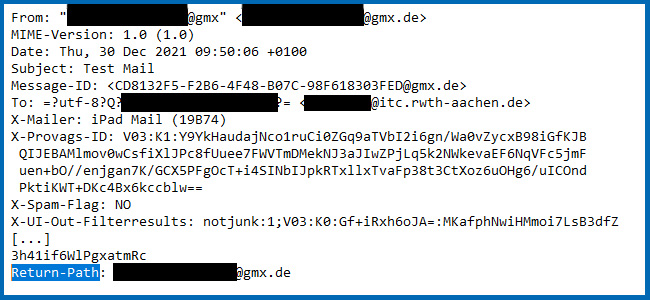
Two other pieces of meta information that contain the sender are the “From-Path” and the “Return-Path” attributes. Normally, all three attributes have the same value. The “From-Path” attribute is displayed to the recipient of an e-mail by the e-mail programme as the sender address. The return-path attribute is used to send a bounce message to the sender in case the e-mail cannot be delivered. This information could look like the following in a mail header:
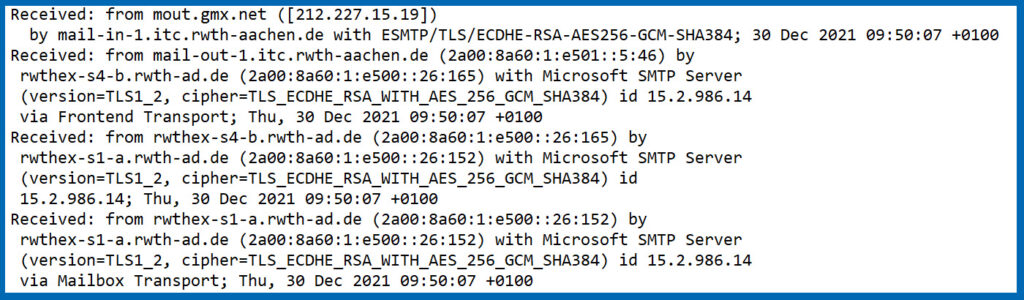
First of all, at the beginning of the mail header is the receive line of the mail server that processed this specific mail. As an example, we list a mail header that contains an e-mail from gmx.de to RWTH Aachen University. In this case, the mail header contains the following information:
In addition to the sending and receiving mail system, a timestamp is also included so that, ideally, the runtime of an e-mail can be determined. This information is written to the mail header during the sending process.
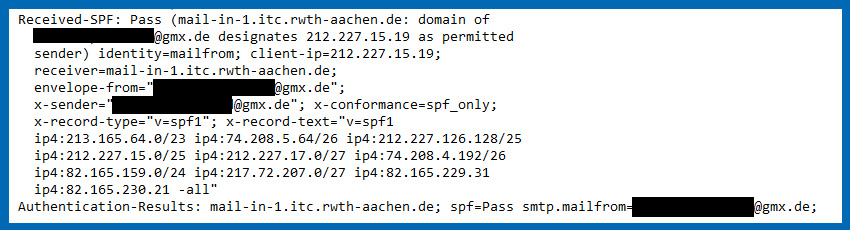
The information in the mail header can be used to check whether an e-mail may be sent from a mail server or whether it is probably a forged e-mail. This procedure is called SPF (Sender Policy Framework) and was published in 2014 via RFC 7208 [1]. Here, an entry is stored in the DNS server [2] for each email domain, which contains a list of email servers that are authorised to send emails for senders of this email domain, so that a receiving mail server can carry out a corresponding check with the help of this entry. RWTH Aachen University introduced this protocol extension a few years ago. Corresponding information about the evaluation can also be found in the mail header:
In another blog post, we will explain to you what else the IT Center has currently implemented in order to be able to manage a secure email exchange for you. Furthermore, in a concluding part we will discuss what we plan to do in the future in order to be prepared for future developments.
Responsible for the content of this article are Morgane Overath und Thomas Pätzold.
[1] RFC: The Requests for Comments are a set of technical and organisational documents related to the Internet. They are numbered documents in which protocols, concepts, methods and programmes of the Internet are treated, described and defined. For example, they form the technical basis of Internet applications such as email.
[2] DNS Server: DNS stands for “Domain Name System”. It is a hierarchical directory system which translates the computer name (Fully-Qualified Domain Name – FQDN) into the corresponding IP addresses. They function, so to speak, as the telephone book of the Internet.