
Source: Freepik
It regularly happens that personal data or other sensitive information such as temporary passwords, application documents etc. need to be transmitted quickly. The choice often falls on the exchange by e-mail. However, this data must be protected against unauthorized access by third parties. In order to still be able to use e-mail, the e-mails must be encrypted. We will show you how this works in the following blog post, along with other relevant information on the subject. Go back to the first blog post in our series to read more about digital signatures.
What Is a Digitally Encrypted Email?
In a digitally encrypted email, the entire content (plain text, HTML text, attachments) is cryptographically encrypted with the recipient’s public key. This makes the content of the email unreadable for everyone except the recipient. To decrypt and thus read the email, the corresponding private cryptographic key of the recipient is required. As long as the recipient’s private key remains “private”, i.e. is never passed on, the email content also remains confidential.

Source: Freepik
How Is an Email Encrypted?
First of all, recipients must have a cryptographic key pair. A key pair consists of the private and public keys, which are algorithmically linked and unique. Such a cryptographic key pair can be generated by applying for a public key certificate (also known as X.509, S/MIME or user certificates), for example at RWTH Aachen University via the RA portal.
This certificate must then be integrated into your own e-mail application (e.g. Outlook, Thunderbird) in the form of a .p12 file. This means that both the private and the public key are known in the e-mail application. This means that the encrypted message received can be decrypted again using the private key and thus made readable.
Public Cryptographic Keys of Recipients
There are two ways to obtain the public key of recipients: The first option is to exchange digitally signed emails. Senders must therefore first send a digitally signed email to the recipient.
This gives them access to the public key, which is part of the sender’s user certificate. As a result, the recipient’s own email application can automatically extract this public key from the email received in the background and save it for sending encrypted emails at a later date.
The second option is to integrate a special address book, the so-called LDAP address book, into your own email program. This address book usually stores the email addresses together with the associated public key certificates. The name of the person is often also stored. This option allows encrypted emails to be sent directly without a prior handshake (receiving a signed email). We will tell you more about the LDAP address book in the third part of the “Email security” series to follow.
How Do I Receive an Encrypted E-mail?
In order to receive an encrypted reply yourself, it is necessary to have a cryptographic key pair. In addition, the email to the recipient should not only be encrypted, but also signed. This way, the recipients can also reply to the sender in encrypted form. Alternatively, it also works if you are listed in an LDAP address book with an email address and public key certificate (more on this in part 3). If only one side has a cryptographic key (S/MIME or user certificate), encryption is therefore only possible in one direction.
Recognizing and Reading Digitally Encrypted Emails
The recipient’s email application recognizes from the email header (digital envelope) that the received email has been digitally encrypted (S/MIME-encrypted message). The recipients themselves can recognize an encrypted email by the lock symbol in the email navigation bar.
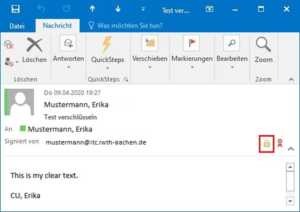
Source: IT Center Help
If the email was encrypted on the sending side with the public key of the receiving side, the content of the email can be decrypted on the receiving side with your own private key and thus “read”. Otherwise, the email is usually displayed as an empty email. The fact that the keys do not belong together and an empty e-mail is displayed can also occur if the computer is changed, for example. This is because the recipient has not yet integrated their own private key into the email application. Please note that all old .p12 files are ported.
Responsible for the content of this article are Mirko Koch, Bernd Kohler, Jelena Nikolić, and Katerina Papachristou.




