In this post of our email security series, we would like to inform you about an upcoming tightening of the SPF policy that will apply to RWTH Aachen University as of December 5, 2024. The change will prevent RWTH email addresses from being used as sender addresses by mail servers outside of RWTH Aachen University in the future. This will further increase email security at our university. Please note that this article is mainly intended for mail administrators of RWTH institutions. (*)
Background: SPF Protocol and Applying of the SPF Policy
In the blog article “Email Security – The SMTP Protocol and Its Problems (Sending and Receiving)” we explained what the SPF protocol is for and how it can be implemented. For RWTH, an SPF record was placed in the DNS for each email domain, containing the IP addresses that are allowed to use sender email addresses from the RWTH domain. An SPF record looks like this:
This DNS record can be used to configure how a receiving mail server should handle emails from a specific domain. For the RWTH domains, we are currently ask the recipient to consult the SPF record for verification.
However, the recipient should check generously. This is indicated by “~All”. This means that we cannot exclude the possibility that different recipients treat our emails differently and reject or accept them, even though the sending IP address is not authorized to send emails with a sender address in the RWTH name space.
We now want to make this policy more binding and change the ~All addition to -All. The minus in front of “All” now means that the SPF record must be checked. This way we advise recipients to reject emails from the RWTH domain if they are sent from an unauthorized IP address. The IT Center hopes that this will improve the email reputation and email security for the employees of the RWTH mail domains in the long run.
When Will the Change Take Place?
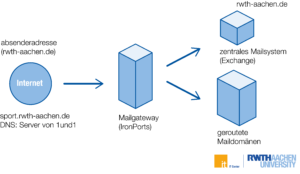
From December 5, 2024, we will evaluate our own SPF record and compare the sender’s email address with the SPF record we may have stored. If the check results in a fail or soft fail, we will reject these emails at the central mail gateway. (**)
What Are the Consequences of the Changeover?
End-users, i.e. students and staff who only use their @[<institute>]rwth-aachen.de or similar address exclusively in their email client (Thunderbird, Smartphone, etc.) should not notice any difference
If RWTH institutions operate systems that send e-mails, e.g. status mails etc., these must be configured to send the e-mails to smarthost.rwth-aachen.de or smarthost-tls.rwth-aachen.de. It is strongly discouraged to use DNS resolution for mail delivery. This would cause the emails to be rejected by us. Furthermore, emails sent from external mail servers with sender addresses from the RWTH name space, e.g. from service providers, will be rejected. Please check this accordingly. If you have implemented such a scenario, please contact us.
Further Information
If you want to learn more about email security, you can get a comprehensive overview in the five blog posts already published in the email security series:
- https://blog.rwth-aachen.de/itc/en/2022/06/15/e-mail-1/
- https://blog.rwth-aachen.de/itc/en/2022/07/27/e-mail-2/
- https://blog.rwth-aachen.de/itc/en/2022/09/07/e-mail-3/
- https://blog.rwth-aachen.de/itc/en/2023/08/30/e-mail-4/
- https://blog.rwth-aachen.de/itc/en/2024/03/13/e-mail-5/
Responsible for the content of this article is Thomas Pätzold.
(*) The chart was updated on November 27, 2024.
(**) The chart was updated on November 27, 2024.