Kategorie: ‘IT-Security’
How can I recognize trustworthy websites?

Source: Pixabay
Surfing the Internet is part of our everyday lives. Both in our private lives and at work, we are using the World Wide Web. We visit websites to inform ourselves, to communicate and even to shop. In the process, data from your own device will automatically be transferred to the website you are visiting and vice versa. When surfing, you should therefore critically inspect every website you visit. Just like in the real world, there are safe places on the Internet and places that you should avoid for your own safety. Nevertheless, how can you judge a website correctly and how can you distinguish between a trustworthy and an untrustworthy website? The following criteria should help you! Read the rest of this entry »
The RWTH email address – your faithful companion to stay up to date

Source: Pixabay
To avoid chaos, in this article we summarize what the RWTH email address is and what else you need to keep in mind around it. Read the rest of this entry »
Dark Data – Data that no one knows about anymore

Source: Unsplash
“Keeping order is not difficult. Cleaning up, on the other hand, is very difficult.” That’s kind of the saying, isn’t it? No matter how you spin the proverb, this principle applies not only to children’s rooms and closets, it also applies to our digital memories, and many people are not yet aware of this. Just because we can’t touch digitized data doesn’t mean it doesn’t waste space or energy. In Germany, around 66 percent of the data held is “dark” and lies below the surface of users’ consciousness. Read this article to find out what this is all about.
Safe on the Internet: Certificate change of RWTH Single Sign-On
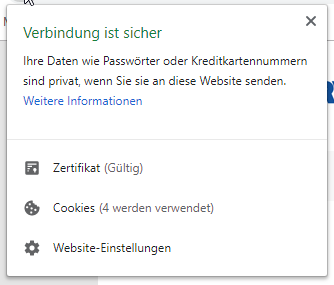
Securely connected? A look at the URL and a click on the lock symbol will show you!
Source: Own illustration
“The connection is secure” – These words contain a short but revealing piece of information. A valid certificate for a website indicates if it has a secure connection and sensitive data, such as passwords or bank data, are transmitted in a protected environment – this is also the case with RWTH Single Sign-On. The certificate for sso.rwth-aachen.de has now been replaced, as the existing one expires on July 28, 2021. Have you noticed this? Some services were temporarily unavailable during the changeover, but are now running again. We’ll show you why it’s worth taking a look at the certificate and what you should keep in mind when using the RWTH Single Sign-On. Read the rest of this entry »
IT-SAD: IT Security Awareness Days 2021!

Online and without any registration – the IT Security Awareness Days 2021
Source: TU Braunschweig
Trustworthy IT infrastructure is essential these days, especially when it comes to IT security. But did you know that most cyber attacks take advantage of human vulnerabilities? Terms like social engineering and (spear-)fishing are becoming more and more popular. In other words, IT security is not limited to the implementation of a solid IT infrastructure. In fact, the human factor can be the greatest vulnerability. Accordingly, it is particularly crucial to involve every single user and to educate them about the various threats.
Safety First – Secure logout with RWTH Single Sign-On
Everyone who studies or works at RWTH knows it: the RWTH Single Sign-On.
This is not a dating service, but an application with which you can log in to almost all RWTH services. What is particularly charming is that you do not have to remember an infinite number of access data, but only one user name and the corresponding password.
In addition, RWTH Single Sign-On recognizes if you are already logged in to a service, for example RWTHonline. If you then log in to RWTHmoodle, RWTH Single Sign-On waves the user through directly using the underlying “Shibboleth” application.
Better Safe Than Sorry – Multifactor-Authentication

Source: Pixabay
In the context of the current pandemic and the latest massive cyberattacks, IT security is more relevant than ever in our daily lives. With many people working from home and using cloud applications to access corporate data, the risk of unauthorised access to this data is growing. . Passwords can be stolen in various manners, ranging from looking over one’s shoulder, a break-in at a service provider on the Internet to malware. Passwords are particularly susceptible to being stolen. Additionally, if you use the same password for multiple services, the quantity of stolen data might be massive. What can we do to ensure our data remains secure?
RWTH mails in the spam folder – why do they end up there and what you can do about it?

Source: Freepik
The spam folder – that place to which undesired emails are banished. This is exactly what the term “spam” refers to: e-mails that you don’t want to receive, which nonetheless keep finding their way into our inbox. Generally, the spam folder is a preset folder provided by the e-mail client, into which unsolicited e-mails are automatically moved with the help of anti-spam software. In fact, most of the time this sorting out works quite well.
(Deutsch) Wie kommt der Banking-Trojaner zu mir? Per E-Mail? NEIN: per SMS!
Macros – Small word, big risk

Source: Unsplash
Every now and then you hear and read about macros in Office applications, about documents in which macros are included. These are often sent by e-mail and can lead to dangerous security incidents.
Of course, RWTH Aachen University and the IT Center have taken security measures in this regard. But not everyone is aware of what macros actually are and how dangerous they are not only for private individuals but also for companies. In the following, we will inform you about the most important risks and explain how you can protect yourself.